Cybersecurity researchers have uncovered a large-scale web skimming operation that has been running quietly since January 2022. The campaign targets online payment environments connected to major card networks, including American Express, Diners Club, Discover, JCB, Mastercard, and UnionPay.
According to a recent report from Silent Push, enterprise-level businesses that rely on these payment providers are the most likely to be affected.
Web skimming, also known as digital skimming, is a client-side attack technique where attackers inject malicious JavaScript into legitimate e-commerce or payment pages. Once embedded, the code secretly captures credit card details and personal information when customers enter payment data during checkout.
These attacks fall under the broader category known as Magecart. The term originally described criminal groups that focused on Magento-based stores, but it has since expanded to include skimming activity across many platforms and technologies.
Silent Push said it identified this campaign while investigating a suspicious domain tied to Stark Industries, a bulletproof hosting provider that has since been sanctioned. The infrastructure later resurfaced under a new brand, THE[.]Hosting, reportedly operated by the Dutch firm WorkTitans B.V., a move believed to be aimed at bypassing sanctions.
The domain, cdn-cookie[.]com, was found hosting heavily obfuscated JavaScript files, such as “recorder.js” and “tab-gtm.js.” These scripts were being loaded directly into online stores, where they functioned as credit card skimmers.
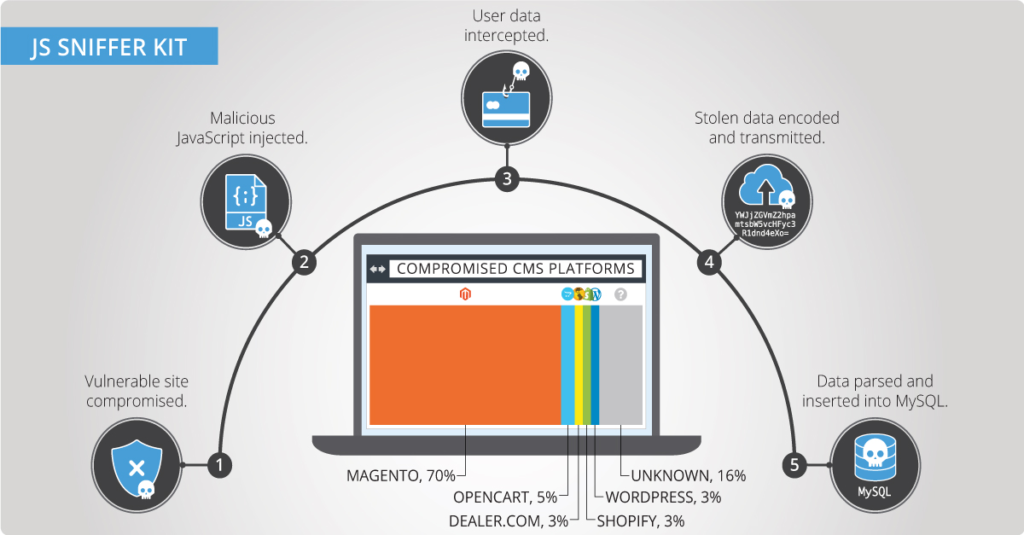
To avoid detection, the malicious code includes several defensive mechanisms. One tactic involves checking the page’s Document Object Model for an element called “wpadminbar,” which typically appears when a WordPress administrator or authorized user is logged in. If this element is detected, the skimmer immediately removes itself from the page.
The script also rechecks the page whenever the DOM changes, which commonly happens as users interact with checkout forms. This allows the skimmer to reattempt execution while remaining hidden from administrators.
In addition, the malware monitors whether Stripe is being used as the payment method. If Stripe is selected and a specific browser storage value called “wc_cart_hash” is not already set, the skimmer creates it and marks it as true after stealing data. This flag prevents the same victim from being targeted more than once.
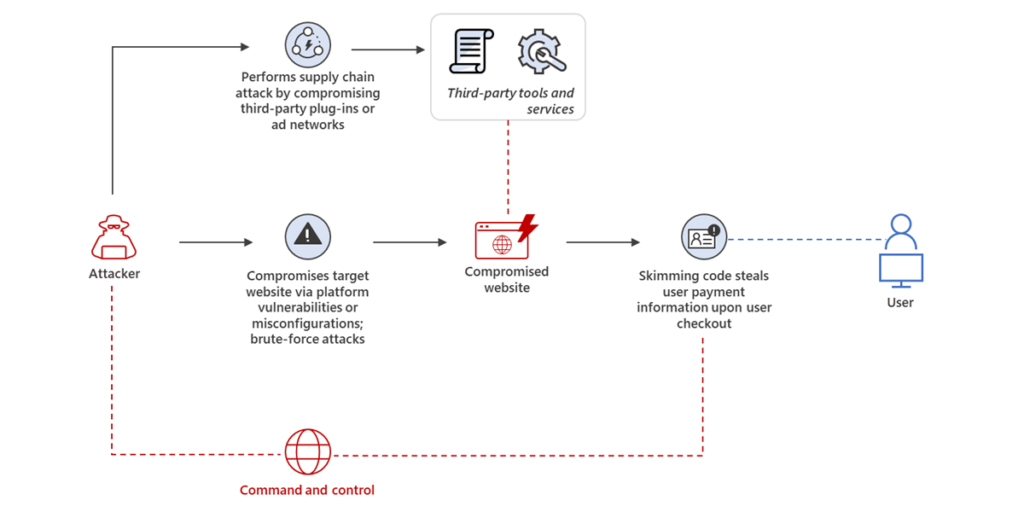
When conditions are met, the attacker’s code replaces the real Stripe payment form with a fake one that looks legitimate. Victims unknowingly enter their card number, expiration date, and CVC into this counterfeit form. After submission, the page displays a generic payment error, making it appear as though the transaction failed due to incorrect details rather than fraud.
Beyond credit card data, the skimmer also collects names, email addresses, phone numbers, and shipping information. The stolen data is then sent via an HTTP POST request to a remote server at lasorie[.]com.
Once exfiltration is complete, the malicious script cleans up after itself. It removes the fake payment form, restores the original Stripe interface, and updates the browser flag to prevent future execution on the same user.
Silent Push noted that the attacker demonstrates deep familiarity with WordPress internals and leverages lesser-known features as part of a highly refined attack chain.

