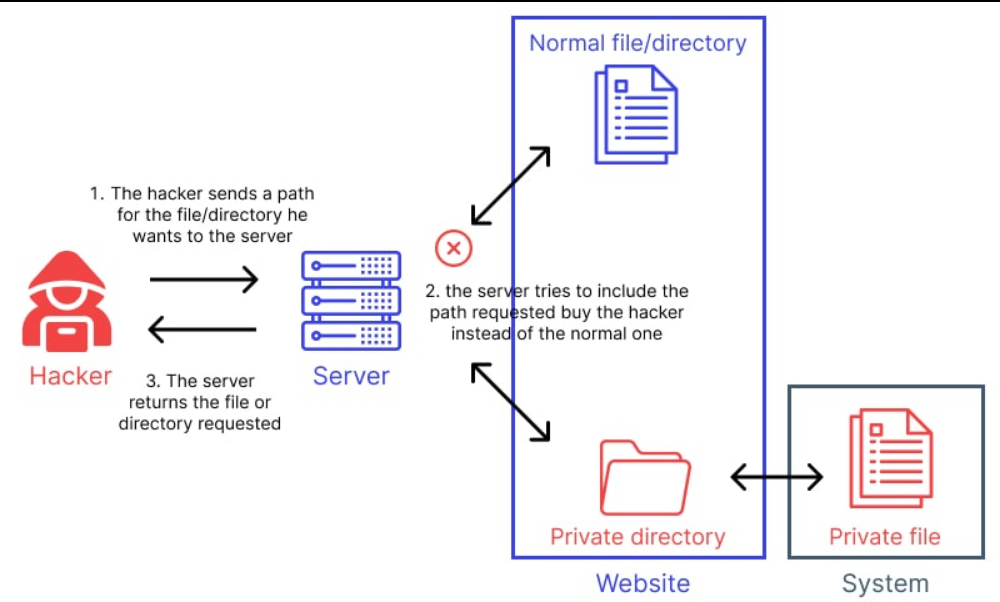
If you’re using the @adonisjs/bodyparser npm package, you should update to the latest version. A newly disclosed high-severity vulnerability could allow a remote attacker to write arbitrary files on your server if they can reach a file upload endpoint.
The issue is tracked as CVE-2026-21440 (CVSS 9.2) and is described as a path traversal flaw in AdonisJS multipart upload handling. @adonisjs/bodyparser is part of the AdonisJS ecosystem and is commonly used to process HTTP request bodies, including file uploads.
What’s happening
The risk centers on the method:
MultipartFile.move(location, options)
Developers often use this function to move an uploaded file into a destination directory. The problem shows up when the file move happens without safely controlling the filename.
In particular, if a developer calls MultipartFile.move() without providing the second options argument, or if they do not explicitly sanitize the filename, the application may fall back to the original client-supplied filename. That filename can be crafted to include traversal patterns (like ../) that could escape the intended upload directory and write files to unexpected locations on the server.
Why that matters
A path traversal that leads to arbitrary file write can be serious on its own, but it can become much worse if the attacker can overwrite files the application later loads or executes.
If an attacker can overwrite things like application code, startup scripts, or configuration files, it can potentially turn into a remote code execution scenario, depending on how the environment is set up and what gets executed later.
When exploitation is possible
This isn’t a “drive-by” bug that affects every site automatically. Exploitation generally requires:
- A reachable upload endpoint
- A server-side flow that moves uploaded files using
MultipartFile.move()in a way that relies on an unsafe filename - In some cases, the ability to overwrite existing files (for example, if overwrite is allowed)
What you should do now
Here are the practical steps to reduce risk:
- Update
@adonisjs/bodyparserto the latest version - Always control the destination filename instead of trusting the client-provided name
- If you use
MultipartFile.move(), pass theoptionsargument and ensure the filename is sanitized - Avoid allowing overwrites unless you truly need it
- Lock down upload endpoints with authentication and validation, especially in admin or internal tools
If your app handles uploads, this is one of those fixes that’s worth doing immediately, then quickly reviewing your upload code to make sure filenames can’t escape the intended folder.