ServiceNow Now Assist Flaw Exposes Enterprises to AI Agent Takeover Attacks
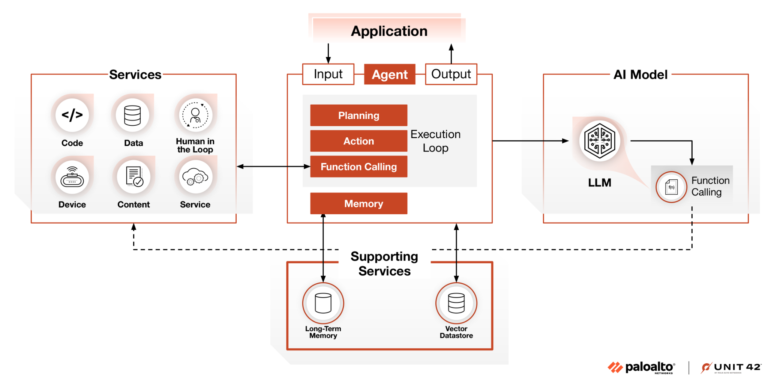
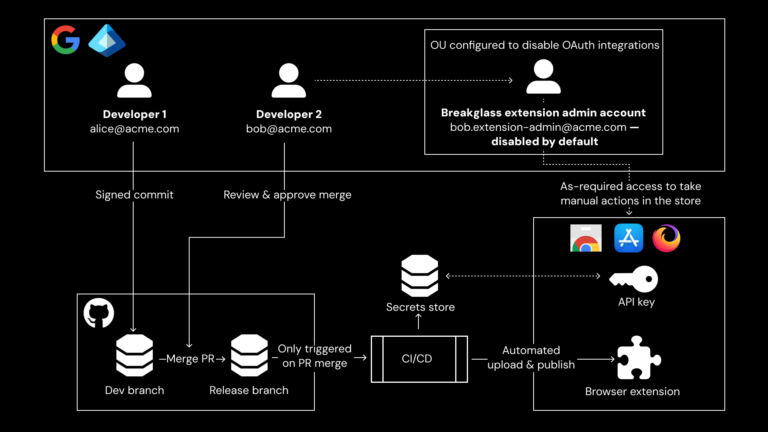
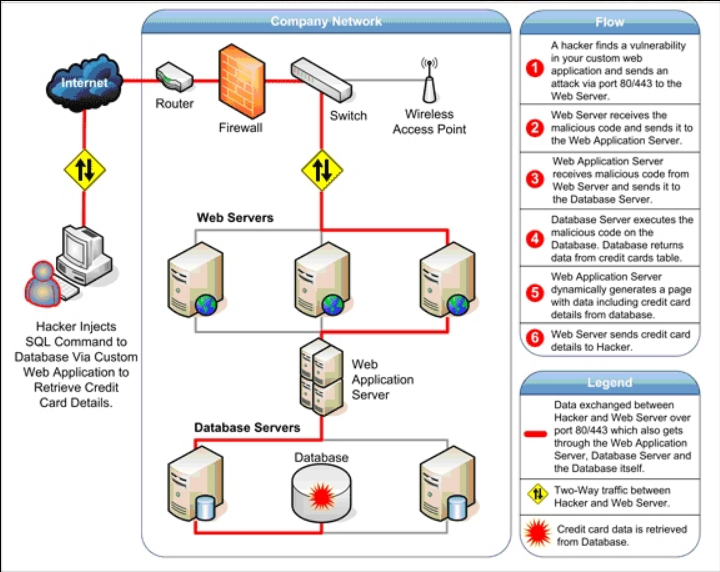
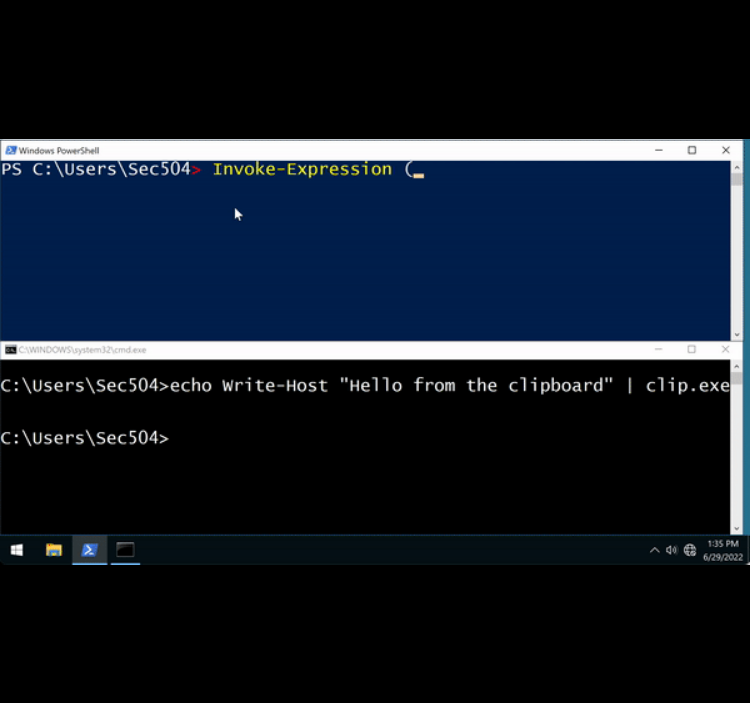
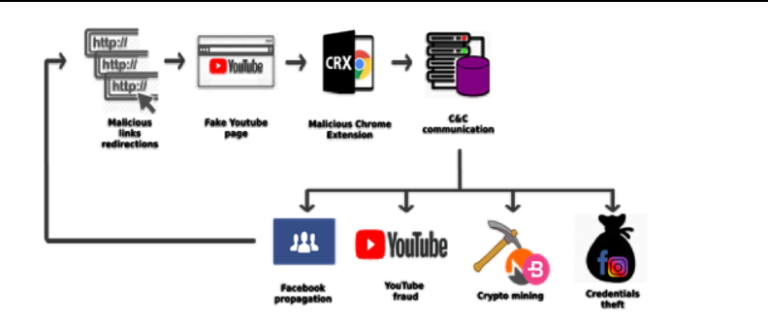
A serious security vulnerability has been identified in ServiceNow that affects its AI and virtual agent components, raising concerns about how agentic AI systems can be abused inside enterprise environments. The issue impacts the following ServiceNow components and versions: The…