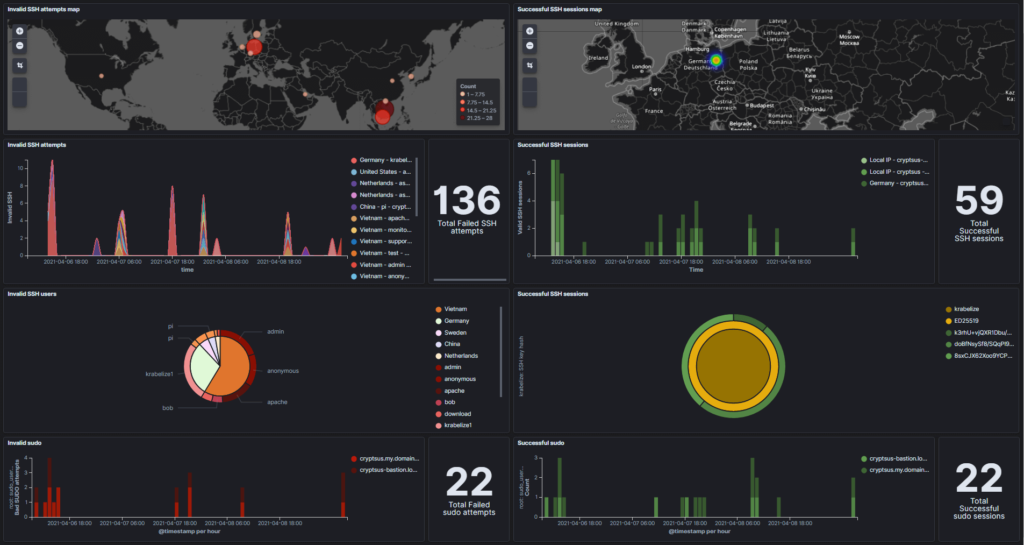
A renewed surge of attacks linked to the GoBruteforcer botnet is actively targeting servers used by cryptocurrency and blockchain projects. The campaign focuses on hijacking poorly secured systems and turning them into part of a distributed botnet used to brute-force login credentials across common services such as FTP, MySQL, PostgreSQL, and phpMyAdmin on Linux-based environments.
Researchers at Check Point Research say the campaign is gaining traction due to two persistent problems: widespread reuse of AI-generated server setup examples that rely on predictable usernames and passwords, and the continued exposure of legacy web stacks like XAMPP that leave administrative services accessible with minimal security controls.
Background on GoBruteforcer
GoBruteforcer, sometimes referred to as GoBrut, was first analyzed by Palo Alto Networks Unit 42 in early 2023. The malware was found to target Unix-like operating systems across x86, x64, and ARM architectures. Once deployed, it installs an IRC-based bot, a web shell for remote access, and a brute-force module designed to scan the internet for additional vulnerable systems.
Later findings from Black Lotus Labs at Lumen Technologies revealed that some systems infected with the SystemBC malware family were also participating in the GoBruteforcer botnet, showing overlap between multiple threat operations.
A More Advanced Variant Emerges
By mid-2025, analysts observed a more advanced Golang-based version of the malware. This iteration includes heavy code obfuscation, improved persistence methods, process-hiding techniques, and dynamically updated credential lists. The malware now uses a redesigned IRC bot written to support multiple platforms more effectively.
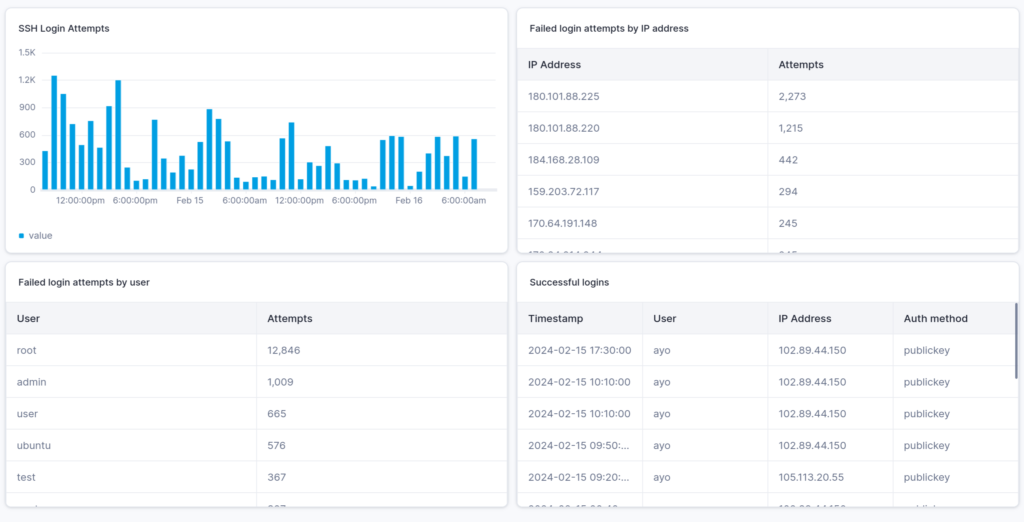
The credential lists used in these attacks combine common usernames and weak passwords that are frequently found in online tutorials, vendor documentation, and example configurations. Because such material is often included in training data for large language models, the same default credentials tend to appear repeatedly in AI-generated deployment scripts.
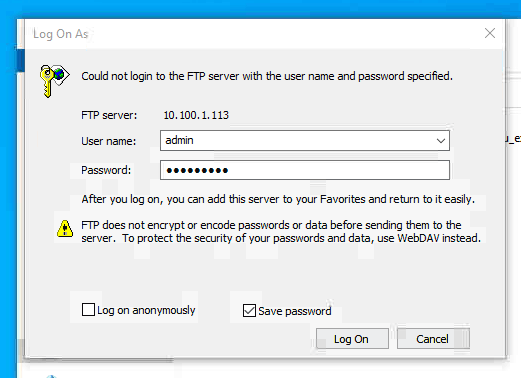
Several usernames are tailored to cryptocurrency environments, while others specifically target phpMyAdmin or content management systems. According to Check Point, attackers rotate usernames frequently while relying on a small, consistent pool of passwords. FTP brute-force attempts stand out because they use a fixed set of credentials embedded directly into the malware, pointing to a focus on default web-hosting setups.
How the Infection Chain Works
In many cases, attackers gain their first foothold through exposed FTP services on servers running XAMPP. After logging in, they upload a PHP-based web shell, which is then used to download and execute an updated IRC bot matched to the system’s architecture.
Once compromised, an infected server may be used in several ways:
- Launch brute-force attacks against FTP, MySQL, PostgreSQL, and phpMyAdmin services
- Host malware payloads for distribution to other victims
- Act as a command-and-control relay or backup C2 server to improve botnet resilience
Investigators also identified at least one compromised host being used to scan TRON blockchain addresses. The system queried balances via a public blockchain API to locate wallets holding funds, suggesting a deliberate effort to identify financially valuable targets within the crypto ecosystem.
A Broader Security Problem
Check Point notes that the effectiveness of GoBruteforcer does not stem from technical sophistication alone. Instead, it thrives because exposed services, weak credentials, and automated attack tools remain widespread across the internet. Even simple malware can scale rapidly when basic security hygiene is ignored.
At the same time, GreyNoise reported a separate but related trend involving large-scale scanning for misconfigured proxy servers that provide access to commercial large language model services.
One campaign observed between October 2025 and January 2026 abused server-side request forgery flaws to probe integrations related to Ollama and Twilio. Based on the infrastructure used, the activity may be tied to security research or bug bounty testing.
A second campaign, beginning in late December 2025, involved aggressive internet-wide scanning to identify exposed LLM endpoints linked to major AI providers, including OpenAI, Google, Meta, Anthropic, and xAI. Over an eleven-day period, more than 80,000 scanning sessions were recorded, pointing to systematic reconnaissance rather than random probing.
Key Takeaway
Together, these findings highlight a growing convergence between weak infrastructure security, automated malware, and the expanding use of AI-driven tools. As attackers continue to capitalize on exposed services and predictable configurations, organizations operating in crypto, AI, and cloud environments face increasing pressure to harden systems, enforce strong authentication, and audit publicly accessible services

