Cybersecurity researchers are warning about a sharp rise in attacks using a technique known as device code phishing, a method increasingly favored by both state-sponsored and criminal hacking groups.
According to a new report from Proofpoint, multiple threat actors — including groups linked to China and Russia — have recently used this technique to compromise Microsoft 365 accounts. Criminal groups have also adopted the same method, making it a growing concern for organizations of all sizes.
Device code phishing works by abusing a legitimate Microsoft authentication process. Instead of stealing passwords directly, attackers trick victims into authorizing access themselves. The attack typically begins with a message that contains a malicious link, often hidden behind a shortened URL or QR code. When clicked, the link leads the victim to a real Microsoft login flow, making the attack appear legitimate.
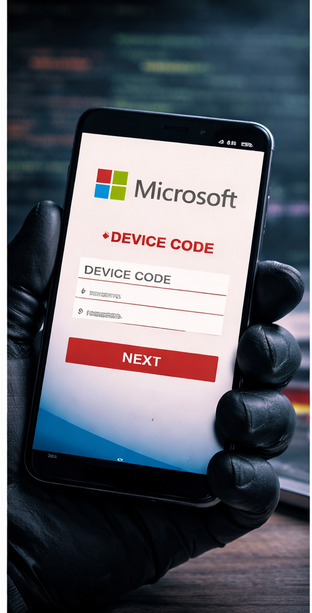
Once the user lands on the page, they are asked to enter a device code provided by the attacker. That code acts as a one-time authentication token. After it is submitted, the attacker gains authorized access to the victim’s Microsoft 365 account without needing a password.
According to Proofpoint researcher Sarah Sabotka, this method is especially dangerous because it exploits trusted systems rather than breaking into them. “It abuses a legitimate authorization process that users are trained to trust,” she explained.
Several hacking tools are being used to carry out these attacks. One is known as SquarePhish2, while another is a phishing framework called Graphish. These tools allow attackers to build convincing login pages and route traffic through infrastructure that helps them stay hidden. Graphish, in particular, uses Azure app registrations and reverse proxy techniques commonly seen in advanced adversary-in-the-middle attacks.
Proofpoint also reported that a threat actor tracked as TA2723 has been selling a malicious toolkit capable of launching device code phishing attacks. Researchers observed activity tied to this actor beginning in early October, with separate campaigns leveraging both SquarePhish2 and Graphish.
In addition, a Russia-linked group known as UNK_AcademicFlare has been connected to a wave of similar attacks. This group has used compromised email accounts from government and military organizations to target victims across government agencies, academic institutions, and transportation sectors in both the United States and Europe.
While Microsoft declined to comment directly on the findings, the company previously published research detailing similar activity tied to a Russia-linked group known as Storm-2372. That campaign, first observed in August 2024, relied heavily on device code phishing and other social engineering tactics. Microsoft has also issued updated security guidance to help organizations defend against these types of threats, particularly those targeting Microsoft Teams and cloud-based identities.
As attackers continue to refine social engineering methods, security experts warn that technical defenses alone are no longer enough. User awareness, stricter access controls, and continuous monitoring are becoming just as critical in protecting modern enterprise environments.

